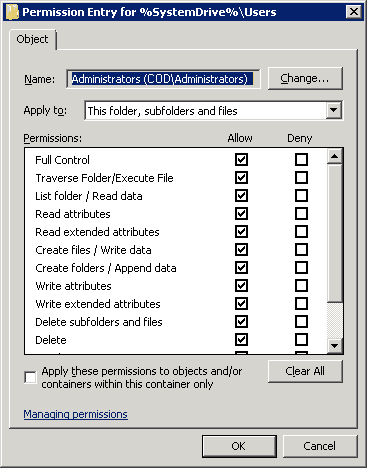
Top 11 NTFS Permissions Tools for Smarter Administration
智能管理的前11个 NTFS 权限工具
Managers and compliance auditors often ask IT admins to present a report listing file share permissions granted to a group or a particular user. Here are a few paid and free tools that will help you save time on generating these reports.
经理和法规遵循审核员经常要求 IT 管理员提交一份报告,列出授予某个组或某个特定用户的文件共享权限。这里有一些付费和免费的工具,可以帮助您节省生成这些报告的时间。
Free Tools for NTFS Reporting and Management
免费的 NTFS 报告和管理工具
1. NTFS Permissions Reporter Free Edition from Cjwdev
1. Cjwdev 的 NTFS 权限报告免费版
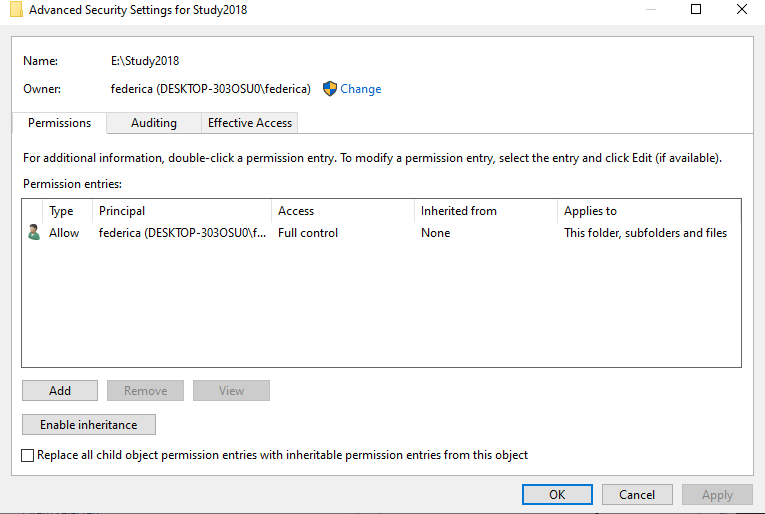
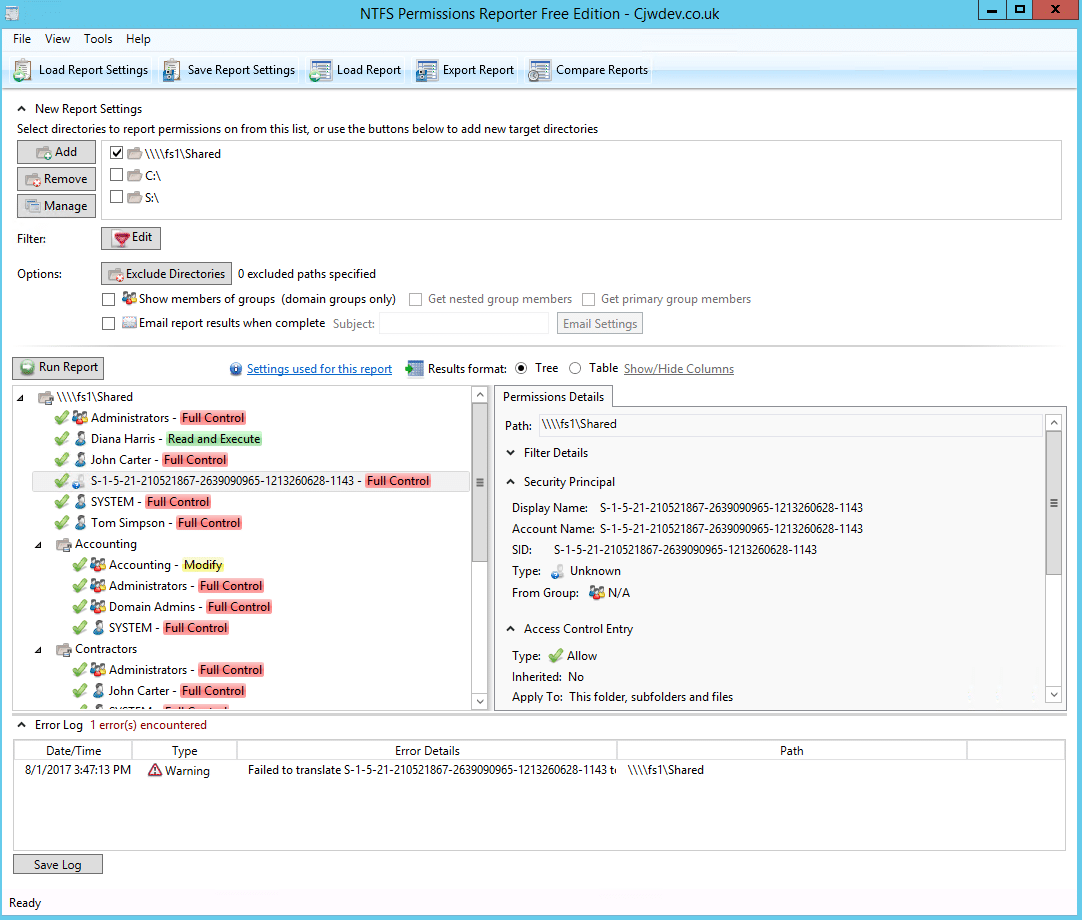
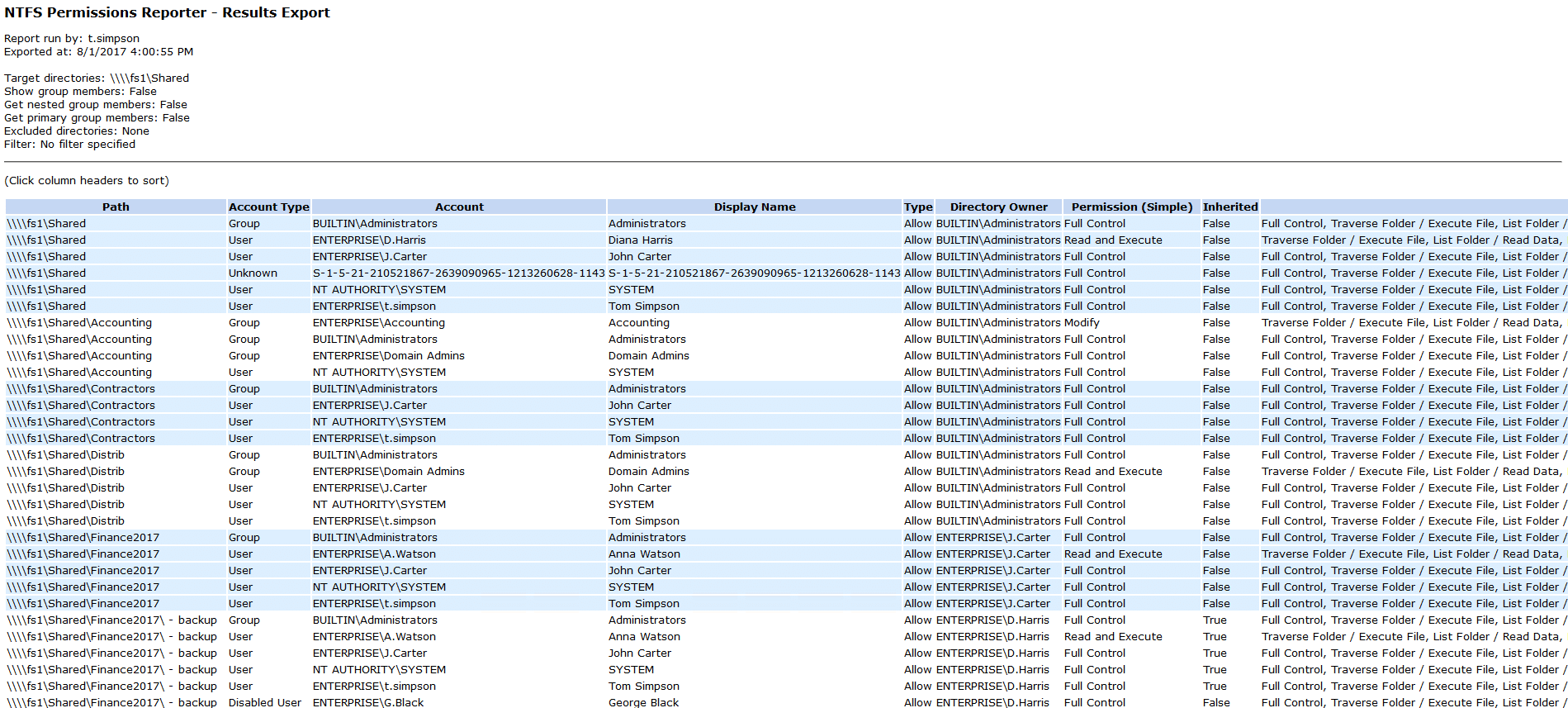
Cjwdev’s NTFS Permissions Reporter is a good tool that helps you export file and folder permissions. It displays group members (direct and nested) right in the report; plus, you can pick the report format (a tree or table) as well as highlight different permissions in different colors. The tool is highly customizable and is rather easy to use, but at first, the interface may look a little overloaded, and permission scanning may take additional time. The tool enables you to easily export report results to an HTML file. However, it creates reports on NTFS permissions only for a folder; it cannot show the permissions of a user.
Cjwdev 的 NTFS 权限报告是一个很好的工具,可以帮助您导出文件和文件夹权限。它在报表中显示组成员(直接的和嵌套的) ; 另外,您可以选择报表格式(树或表格)以及以不同的颜色突出显示不同的权限。这个工具是高度可定制的,并且相当容易使用,但是首先,界面可能看起来有点过载,并且权限扫描可能需要额外的时间。该工具使您能够轻松地将报告结果导出到 HTML 文件。但是,它只为文件夹创建 NTFS 权限报告; 它不能显示用户的权限。
2. Netwrix Effective Permissions Reporting Tool
2. netrix 有效权限报告工具
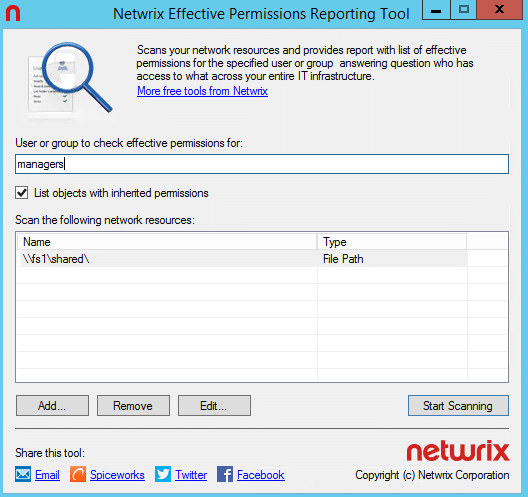
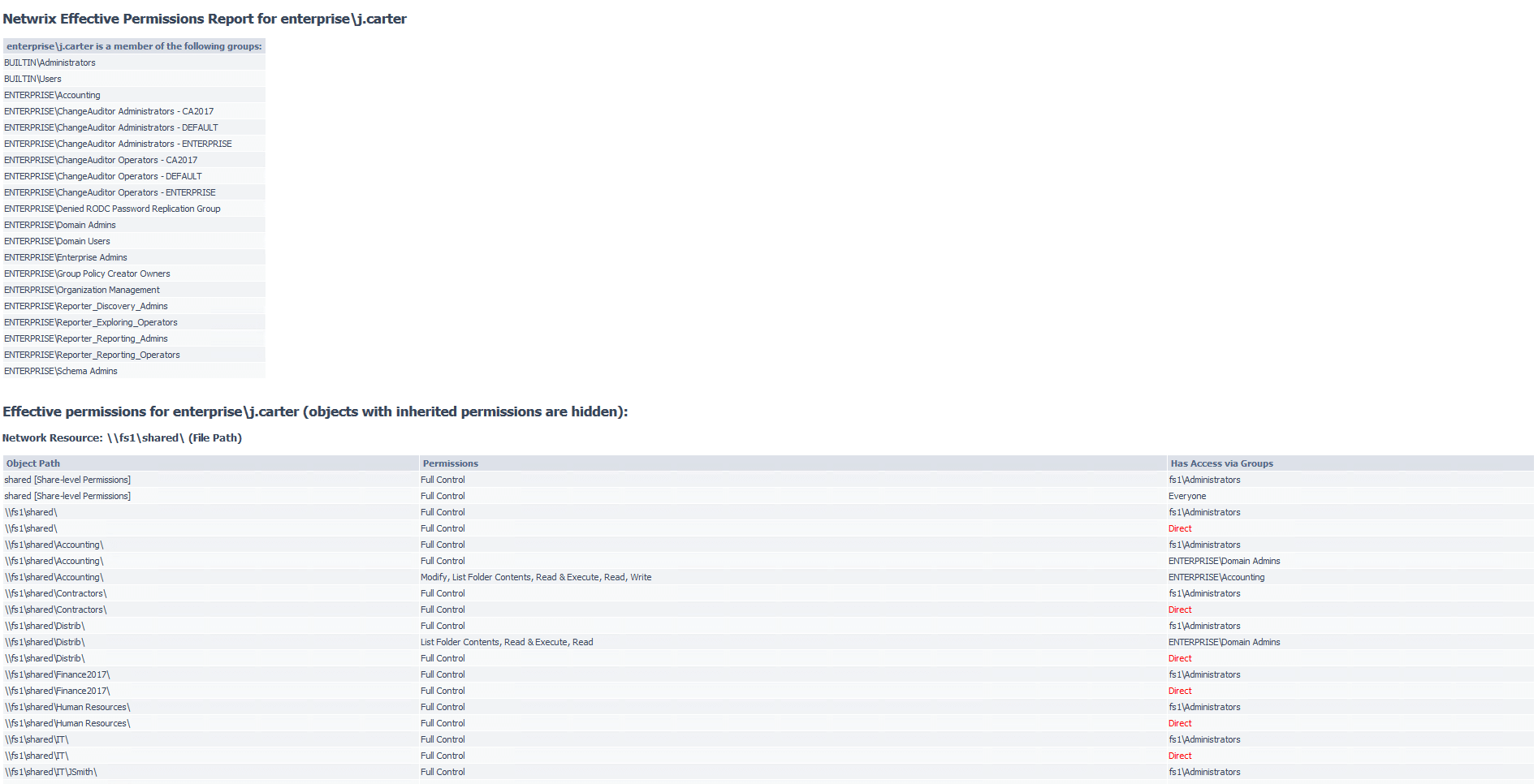
Netwrix Effective Permissions Reporting Tool helps you make sure that employees’ permissions align with their roles in the organization. IT delivers a file share and Active Directory permissions report that details who has access to what and how that access was gained. This freeware tool is very simple and easy to use: You just need to enter the name of a user or group to check its permissions. The scan is very fast and the HTML export functionality is straightforward. It doesn’t show folder permissions, however; such a report is available in Netwrix Auditor for File Servers (20-day free trial).
Netwrix 有效权限报告工具可以帮助您确保员工的权限与他们在组织中的角色相一致。IT 提供了一个文件共享和 activedirectory 权限报告,其中详细说明了谁可以访问哪些内容以及如何访问。这个免费软件工具非常简单易用: 您只需输入一个用户或组的名称,以检查其权限。扫描速度非常快,HTML 导出功能非常简单。但是,它不显示文件夹权限; 这样的报告可以在 netwright Auditor for File Servers (20天免费试用期)中获得。
3. Microsoft’s Access Enum 3. 微软的 Access Enum
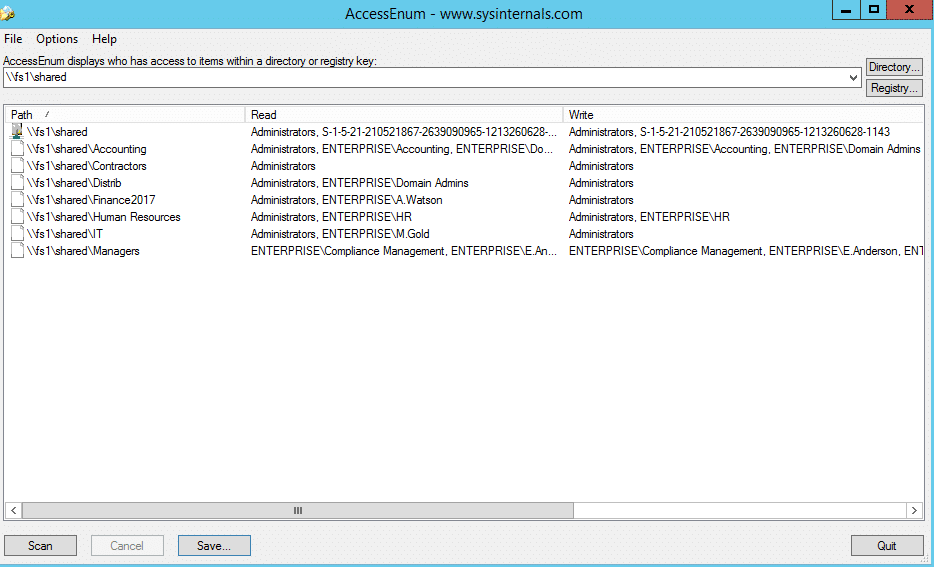
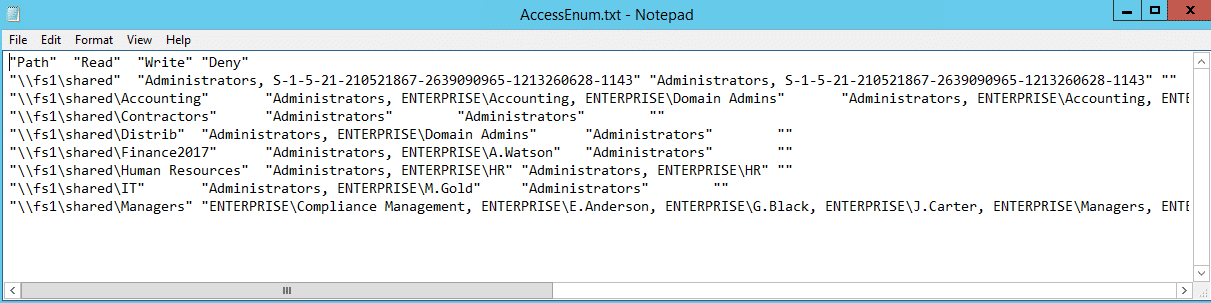
As there’s no built-in way to quickly view user accesses to a tree of directories or keys, Microsoft Windows SysInternals tools may come handy. AccessEnum is one of SysInternals tools which gives you a full view of your file system and Registry security settings in seconds, and provides a table view of all permissions on your file share or registry. However, you can export only to .txt format, which is rather complicated to read. If you want the information in .xls format, you’ll need to copy it from the .txt file manually.
由于没有快速查看用户访问目录树或键的内置方法,Microsoft Windows SysInternals 工具可能会派上用场。AccessEnum 是 SysInternals 工具之一,它可以在几秒钟内提供文件系统和注册表安全设置的全景,并提供文件共享或注册表上所有权限的表格视图。但是,您只能将。格式,这是相当复杂的阅读。如果你想要这些信息。Xls 格式,你需要从。Txt 文件手动。
4. Permissions Reporter from Key Metric Software
4. 来自关键度量软件的权限报告
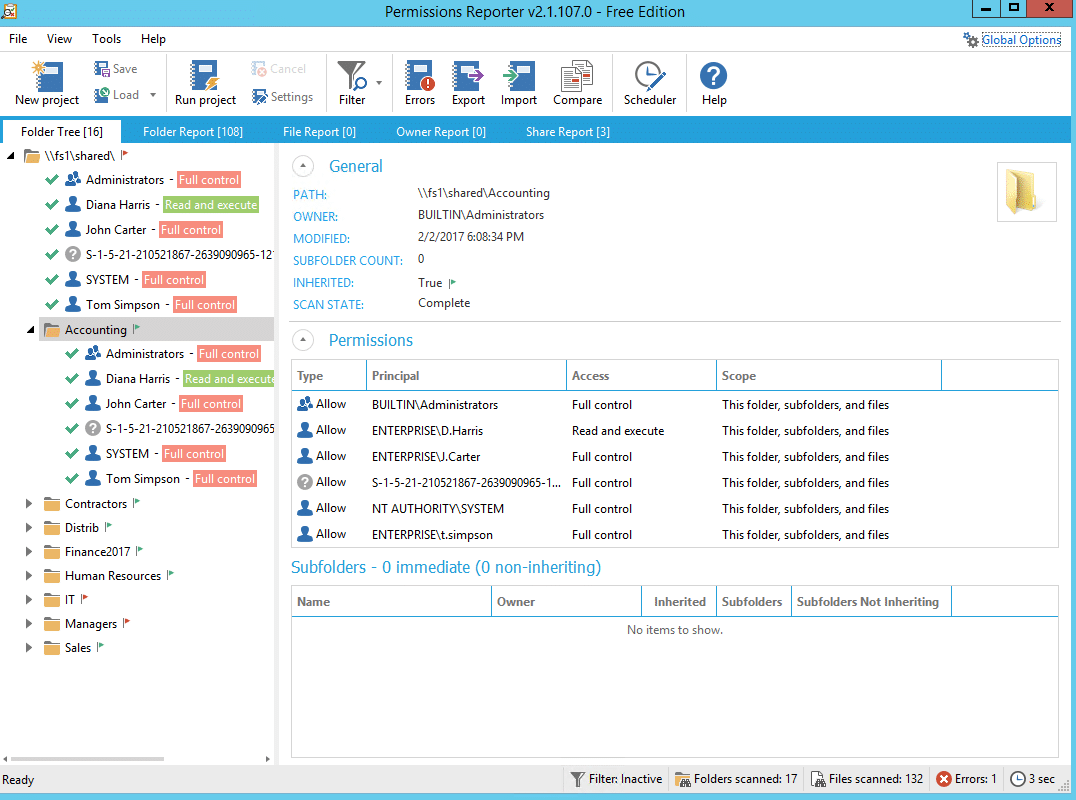
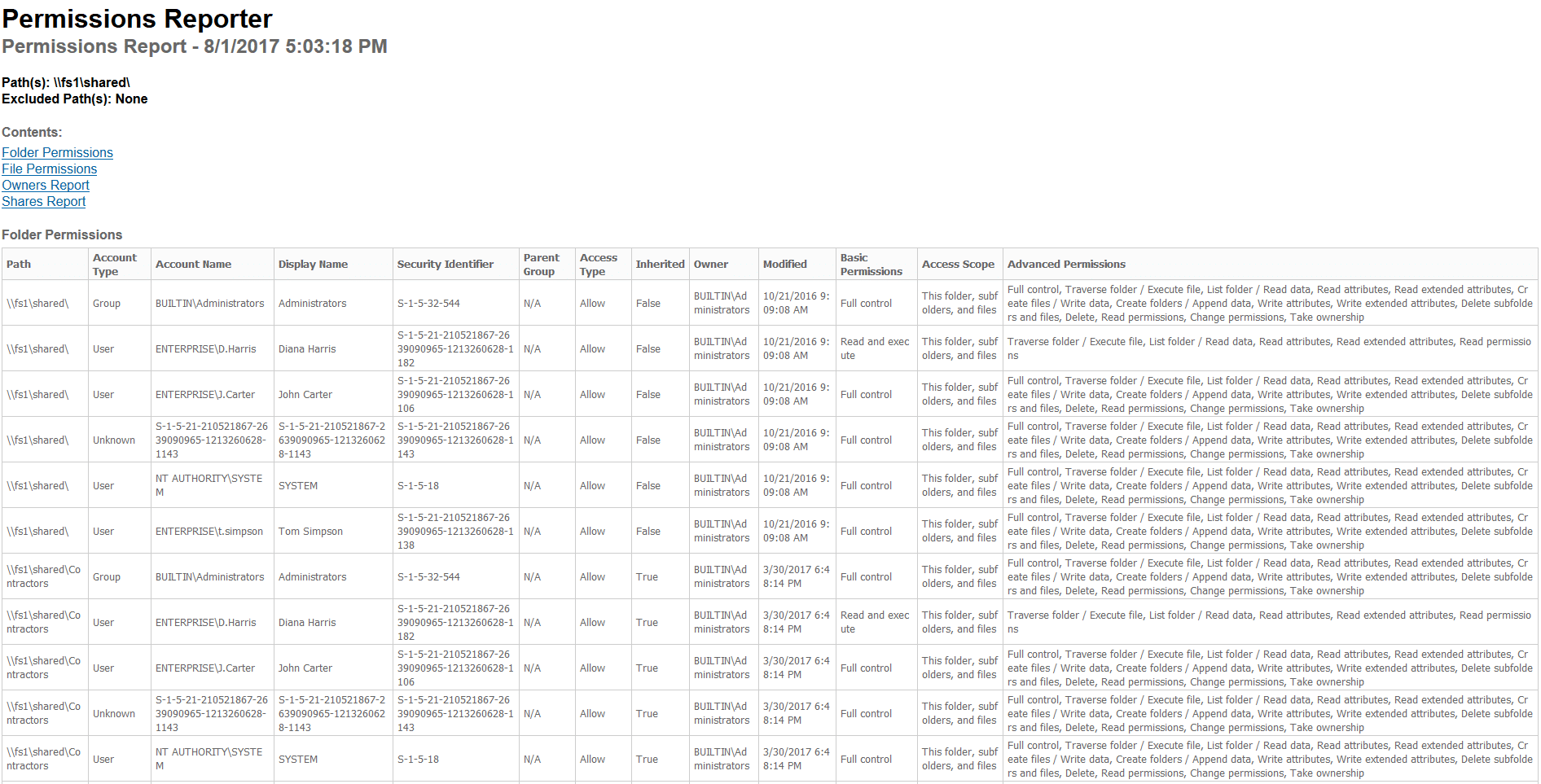
Permissions Reporter is a very good Windows NTFS permissions reporting tool. It has the same functionality as Cjwdev’s NTFS Permissions Reporter tool, but has a prettier interface. It’s also easy to create and download repots. However, permission scanning takes some time, and you can report on only NTFS permissions to a folder or a HTML file, not the permissions of a user.
权限报告是一个非常好的 Windows NTFS 权限报告工具。它具有与 Cjwdev 的 NTFS 权限报告工具相同的功能,但界面更加漂亮。创建和下载 repots 也很容易。但是,权限扫描需要一些时间,您只能报告对文件夹或 HTML 文件的 NTFS 权限,而不能报告用户的权限。
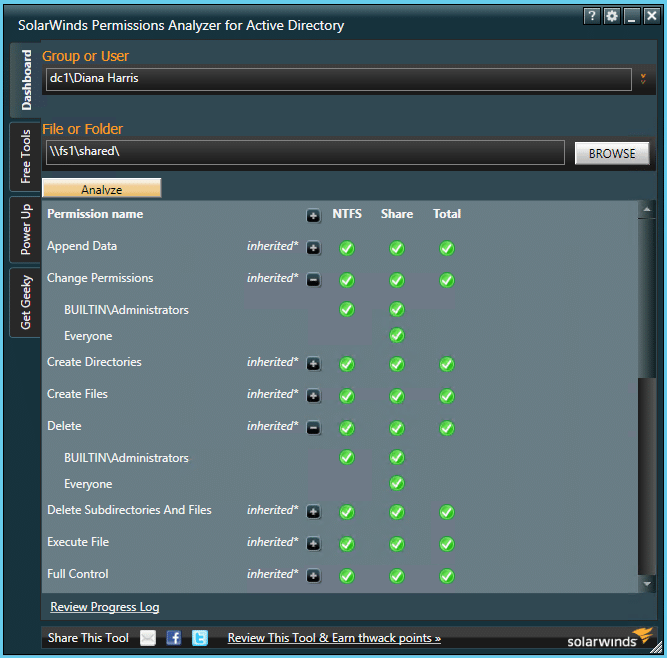
5. Permissions Analyzer from SolarWinds 5. SolarWinds 的权限分析器
Some users might not be fond of Permissions Analyzer because you cannot export information from it, but for those who just need detailed information about user permissions, it can be rather handy. It quickly identifies how users’ permissions were inherited, browses permissions by group or by individual user, and analyzes them based on group membership and permissions.
有些用户可能不喜欢 Permissions Analyzer,因为您无法从它导出信息,但对于那些只需要关于用户权限的详细信息的用户来说,它可能相当方便。它快速识别用户的权限是如何继承的,按组或单个用户浏览权限,并根据组成员和权限分析这些权限。
6. NTFS Permissions Tools from MajorGeeks.com
6. majorgeeks 网站的 NTFS 权限工具
NTFS Permissions Tools offers file permissions management for NTFS file systems. This handy tool was made for admins who need a lightweight access rights manager — it enables you to make a lot of permissions and security changes at once. Its main advantage over Window’s built-in permission and security tool is that it takes less time to change permissions and security settings.
NTFS 权限工具为 NTFS 文件系统提供文件权限管理。这个方便的工具是为需要轻量级访问权限管理器的管理员开发的ー它使您能够同时进行许多权限和安全更改。与 Window 的内置权限和安全工具相比,它的主要优势在于更改权限和安全设置所需的时间更少。
BONUS Free Tool: Microsoft PowerShell 免费工具: Microsoft PowerShell
If you prefer, you can always rely on your old friend PowerShell. Here are ready-to-use scripts for exporting folder permissions and user permissions into .csv format.
如果你愿意,你可以依靠你的老朋友 PowerShell。下面是用于导出文件夹权限和用户权限的现成脚本。Csv 格式。
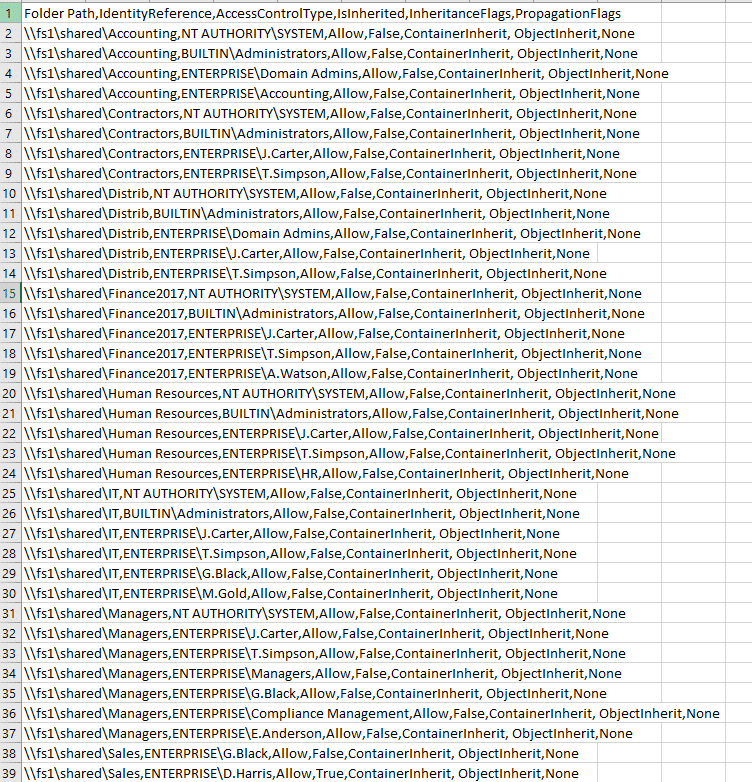
PowerShell code for exporting folder permissions
用于导出文件夹权限的 PowerShell 代码
$OutFile = "C:\Temp\permissions.csv"
$Header = "Folder Path,IdentityReference,AccessControlType,IsInherited,InheritanceFlags,PropagationFlags"
Del $OutFile
Add-Content -Value $Header -Path $OutFile
$RootPath = "\\fs1\shared"
$Folders = dir $RootPath -recurse | where {$_.psiscontainer -eq $true}
foreach ($Folder in $Folders){
$ACLs = get-acl $Folder.fullname | ForEach-Object { $_.Access }
Foreach ($ACL in $ACLs){
$OutInfo = $Folder.Fullname + "," + $ACL.IdentityReference + "," + $ACL.AccessControlType + "," + $ACL.IsInherited + "," + $ACL.InheritanceFlags + "," + $ACL.PropagationFlags
Add-Content -Value $OutInfo -Path $OutFile
}}
Sample report:
样本报告:
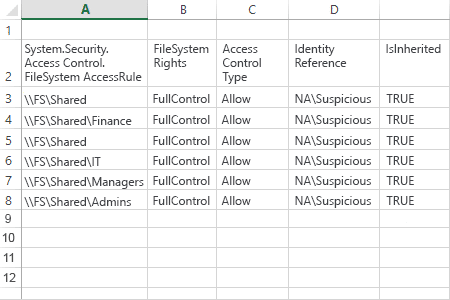
PowerShell code for exporting user permissions
用于导出用户权限的 PowerShell 代码
"ENTERPRISE\J.Carter" } | Add-Member -MemberType NoteProperty -name "\\fs1\shared\" -Value $path1 -passthru }} | export-csv "C:\temp\permissions.csv"
Sample report:
样本报告:
Paid Tools for NTFS Reporting and Management
用于 NTFS 报告和管理的付费工具
1. Jam Software’s TreeSize
Jam Software’s TreeSize is focused on storage analysis. There is a limited freemium licensing option and a 30-day free trial of the full version.
Jam Software 的 TreeSize 专注于存储分析。有一个有限的免费增值许可选项和30天的完整版免费试用。
The free edition is highly praised by IT admins for its high scan speeds, ability to process and analyze storage (including network drives and locally synchronized cloud drives), and option to break down scan results according to owner, file type, size, etc., throughout the entire file system. For instance, this tool can help admins find largest files, the oldest files and the files with long paths.
免费版本因其高速的扫描速度、处理和分析存储(包括网络驱动器和本地同步云驱动器)的能力以及根据所有者、文件类型、大小等在整个文件系统中分解扫描结果的选项而受到 IT 管理员的高度赞扬。例如,这个工具可以帮助管理员找到最大的文件、最旧的文件和路径较长的文件。
The paid version also analyses file owners and permissions, NTFS compression rate, and much more. It can also process NTFS Alternate Data Streams and NTFS Hardlinks, will export scan results to various file formats, and provides command-line automation options.
付费版本还分析文件所有者和权限,NTFS 压缩率,等等。它还可以处理 NTFS 备用数据流和 NTFS 硬链接,将扫描结果导出到各种文件格式,并提供命令行自动化选项。
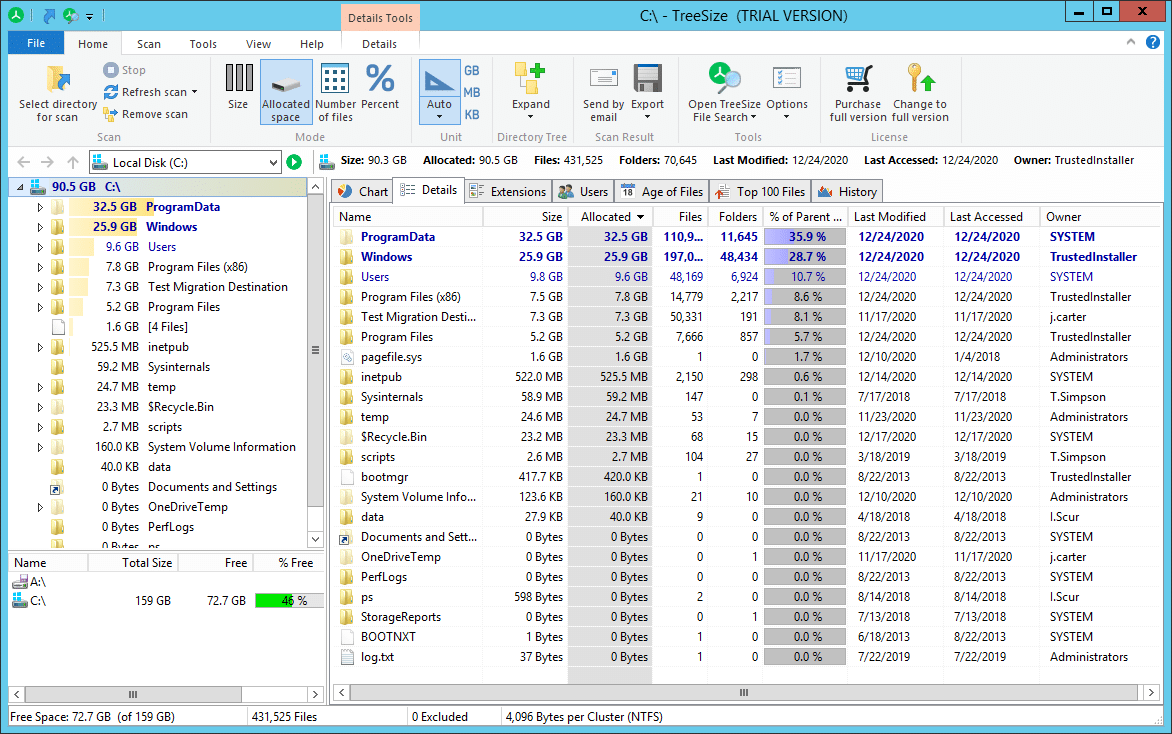
2. Netwrix Auditor for File Servers
2. 文件服务器网络审计员
Netwrix Auditor for Windows File Servers delivers deep visibility into your Windows file servers, including permissions. Its various state-in-time reports provide a complete picture of effective permissions, duplicate files and stale data across your Windows file servers. It delivers visibility into all changes and all access events (both successful and failed) across your file storages, so you can compare your settings against your privacy policy and detect privilege escalation before any damage is done. Its ready-to-use reports streamline NTFS permissions audits and compliance reporting for requirements such as PCI DSS, SOX and HIPAA.
用于 Windows 文件服务器的 netrixauditor 提供了对 Windows 文件服务器的深度可见性,包括权限。它的各种状态实时报告提供了有效权限、重复文件和 Windows 文件服务器上的陈旧数据的完整图片。它提供了所有更改和所有访问事件的可见性(包括成功和失败的) ,所以你可以比较你的设置和你的隐私政策,并在任何损害发生之前检测权限提升。其随时可用的报告简化了 NTFS 权限审计和符合性报告,例如 PCI DSS、 SOX 和 HIPAA。
In conjunction with file analysis technology, it also helps you to stay aware of all changes to Windows Server file permissions; determine effective permissions by user and by object across multiple file servers and shares; and understand whether those file permissions were assigned directly or via group membership.
结合文件分析技术,它还可以帮助您了解 Windows Server 文件权限的所有更改; 确定跨多个文件服务器和共享的用户和对象的有效权限; 以及了解这些文件权限是直接分配的还是通过组成员身份分配的。
There is a 20-day free trial.
免费试用20天。
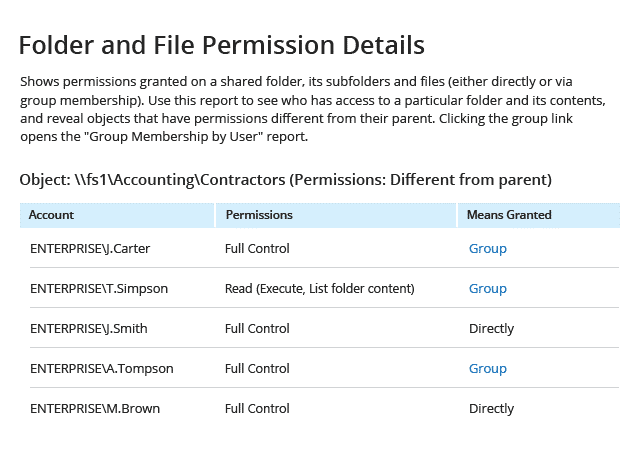
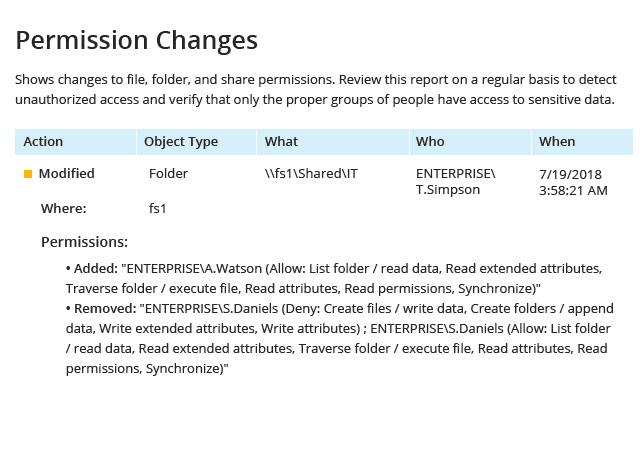
3. AlbusBit’s NTFS Permissions Auditor
3. AlbusBit 的 NTFS 权限审计员
NTFS Permissions Auditor allows you to review and analyze any NTFS folder permissions. While the free version provides you with audit data, such as full path, owner, last modified, inherited flag and a full list of permissions in hierarchical folder view or account view, the pro version offers additional features such as report filtering by fields such as account name, SID or department; permission change analysis; export to various formats; report customization; automation; and more.
NTFS 权限审核允许您查看和分析任何 NTFS 文件夹权限。免费版本提供审计数据,比如完整路径、所有者、最后修改、继承标志以及分层文件夹视图或帐户视图中的完整权限列表,而专业版本提供其他特性,比如按帐户名、 SID 或部门等字段进行报告过滤; 权限更改分析; 导出到各种格式; 报告定制; 自动化; 等等。
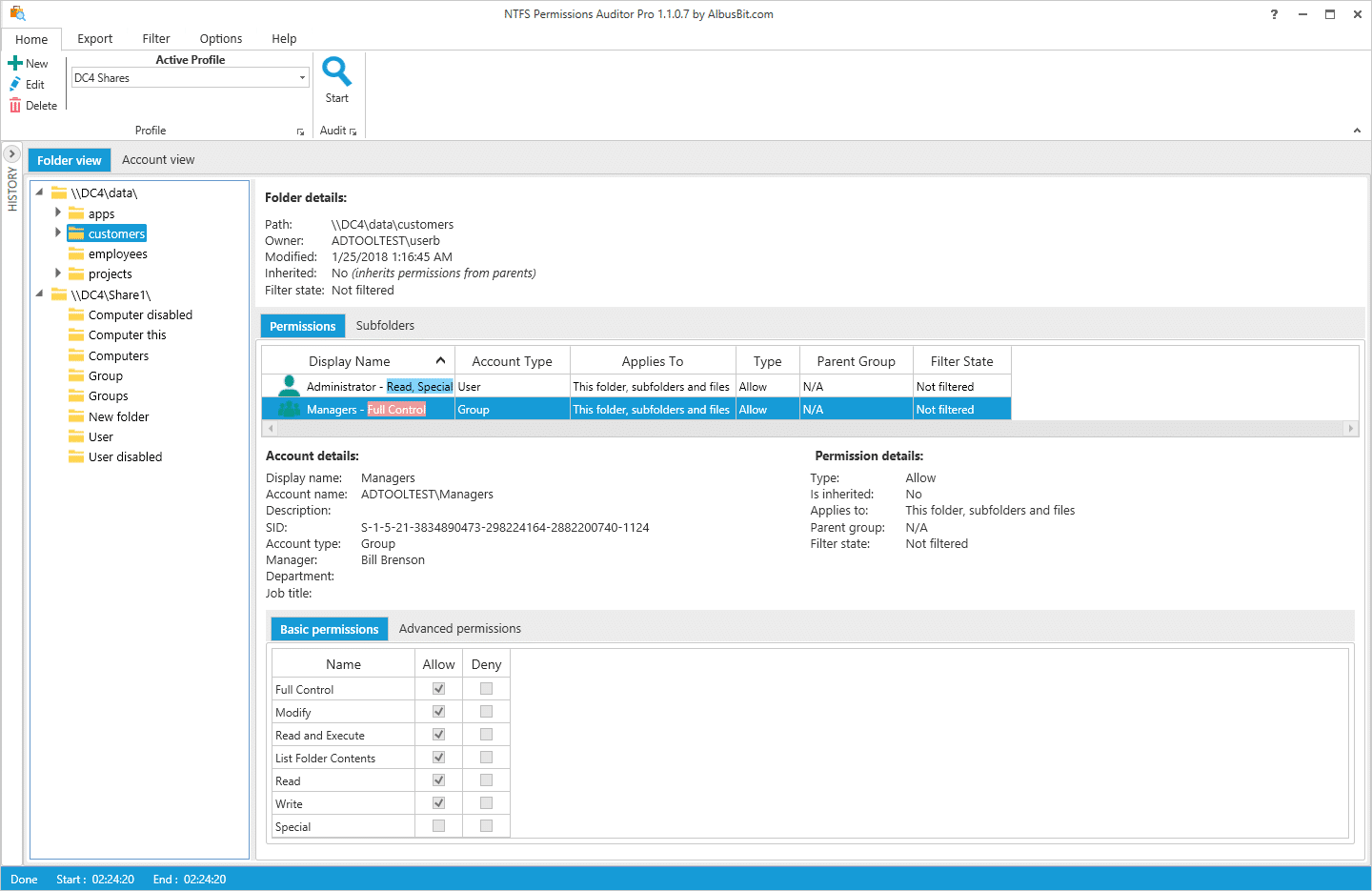
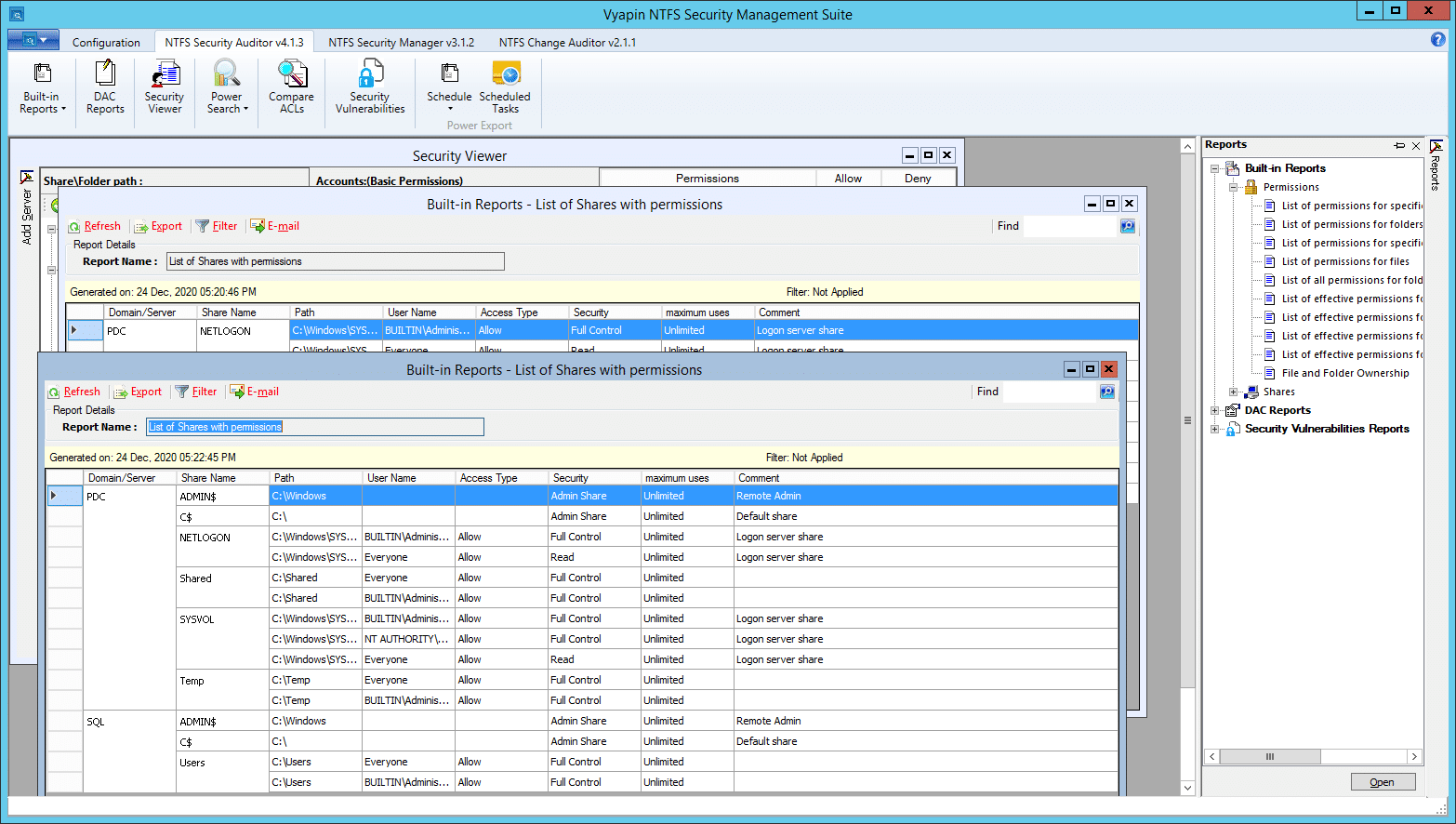
4. Vyapin’s NTFS Security Management Suite
4. Vyapin 的 NTFS 安全管理套件
NTFS Security Management Suite is more like a full-fledged NTFS management system than single-task NTFS permission tool. It consists of three modules:
NTFS 安全管理套件比单任务 NTFS 权限工具更像是一个成熟的 NTFS 管理系统。它由三个单元组成:
- NTFS Security Auditor enables you to scan shares, folders and files in your network, perform an automated inventory of permissions at regular intervals, and compare ACLs. There are a variety of built-in reports for system administrators and compliance
- NTFS 安全审计员使您能够扫描共享,文件夹和文件在您的网络,执行一个定期的权限自动清单,并比较 acl。对于系统管理员和遵从性,有各种内置的报告
- NTFS Change Auditor collects and analyses permission changes on specified locations.
- NTFS 变更审核员收集和分析指定位置的许可变更。
- NTFS Security Manager is designed to simplify native permission management.
- NTFS 安全管理器旨在简化本机权限管理。
Vyapin provides a 15-day evaluation copy of NTFS Security Management Suite.
Vyapin 提供一个 NTFS 安全管理套件的15天评估副本。
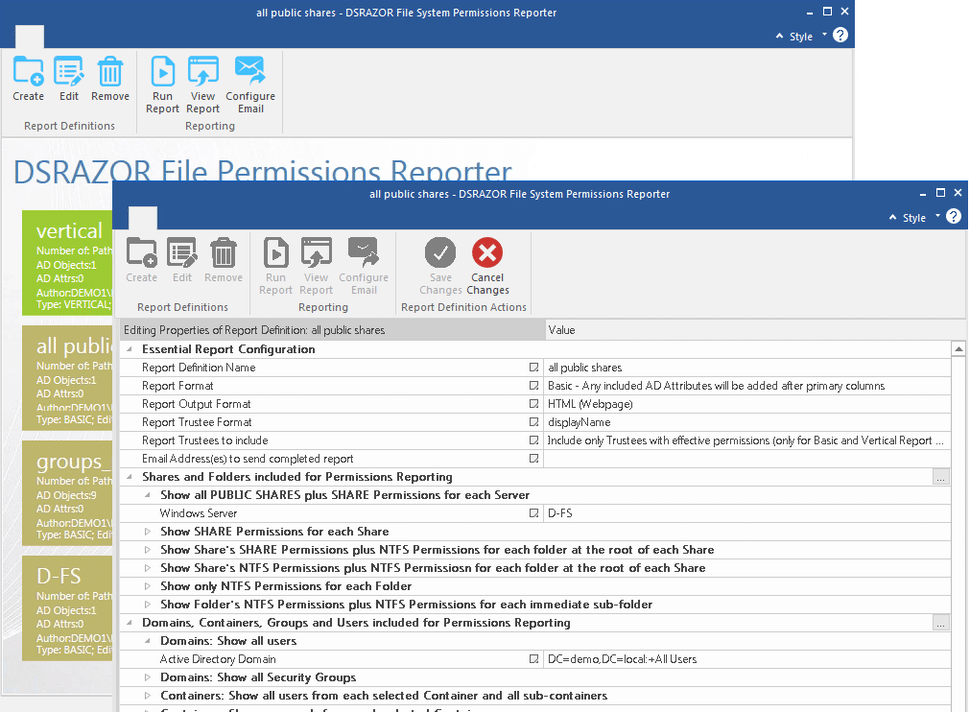
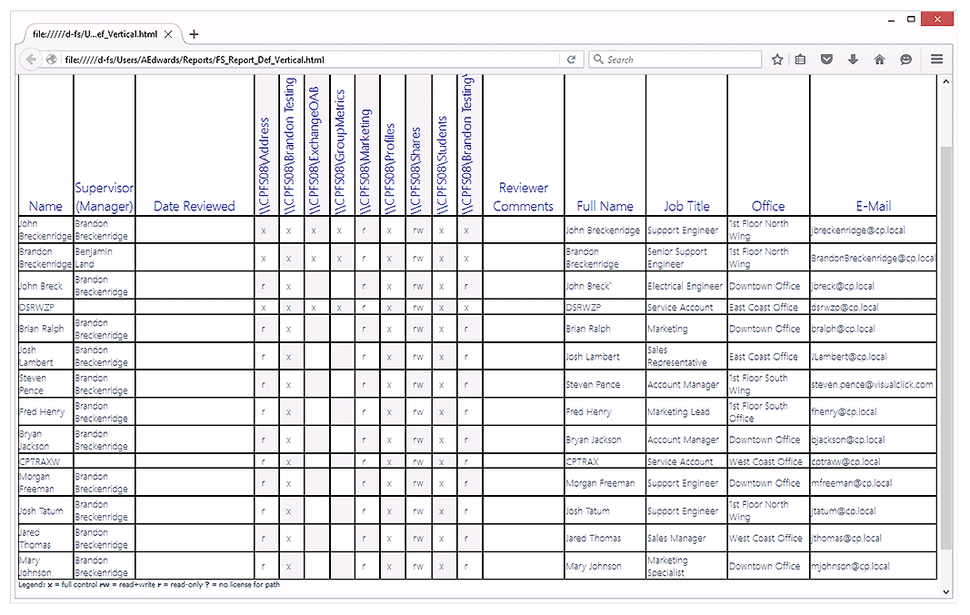
5. DSRAZOR from Visual Click Software
5. 来自 Visual Click Software 的 DSRAZOR
DSRAZOR is a versatile and customizable reporting tool for administrators and compliance auditors. You can analyze permissions for a particular file or folder. Reports are customizable and can include specific Active Directory attributes for each trustee, so auditors can tailor reports to their particular needs. There are comprehensive reports on past due, blocked or deactivated Active Directory accounts, and you can find out which accounts are not in use during a particular period, where the last login failed, and much more. However, while DSRASOR praised by many for its versatility, there is a fairly steep learning curve — the report design tool is rather clunky, and overall setup process is not super user-friendly.
DSRAZOR 是一个面向管理员和合规审计员的多功能和可定制的报告工具。您可以分析特定文件或文件夹的权限。报告是可定制的,可以为每个受托人包含特定的 activedirectory 属性,因此审计员可以根据自己的特定需求定制报告。这里有关于过期、被阻止或停用的活动目录帐户的综合报告,你可以找出哪些帐户在某个特定的时间段内没有使用,哪些帐户上次登录失败,等等。然而,尽管 DSRASOR 的多功能性受到了许多人的称赞,但它的学习曲线却相当陡峭ーー报表设计工具相当笨拙,整个设置过程也不是非常用户友好。

 English
English
 中文
中文